Analysis of LockBit ransomware
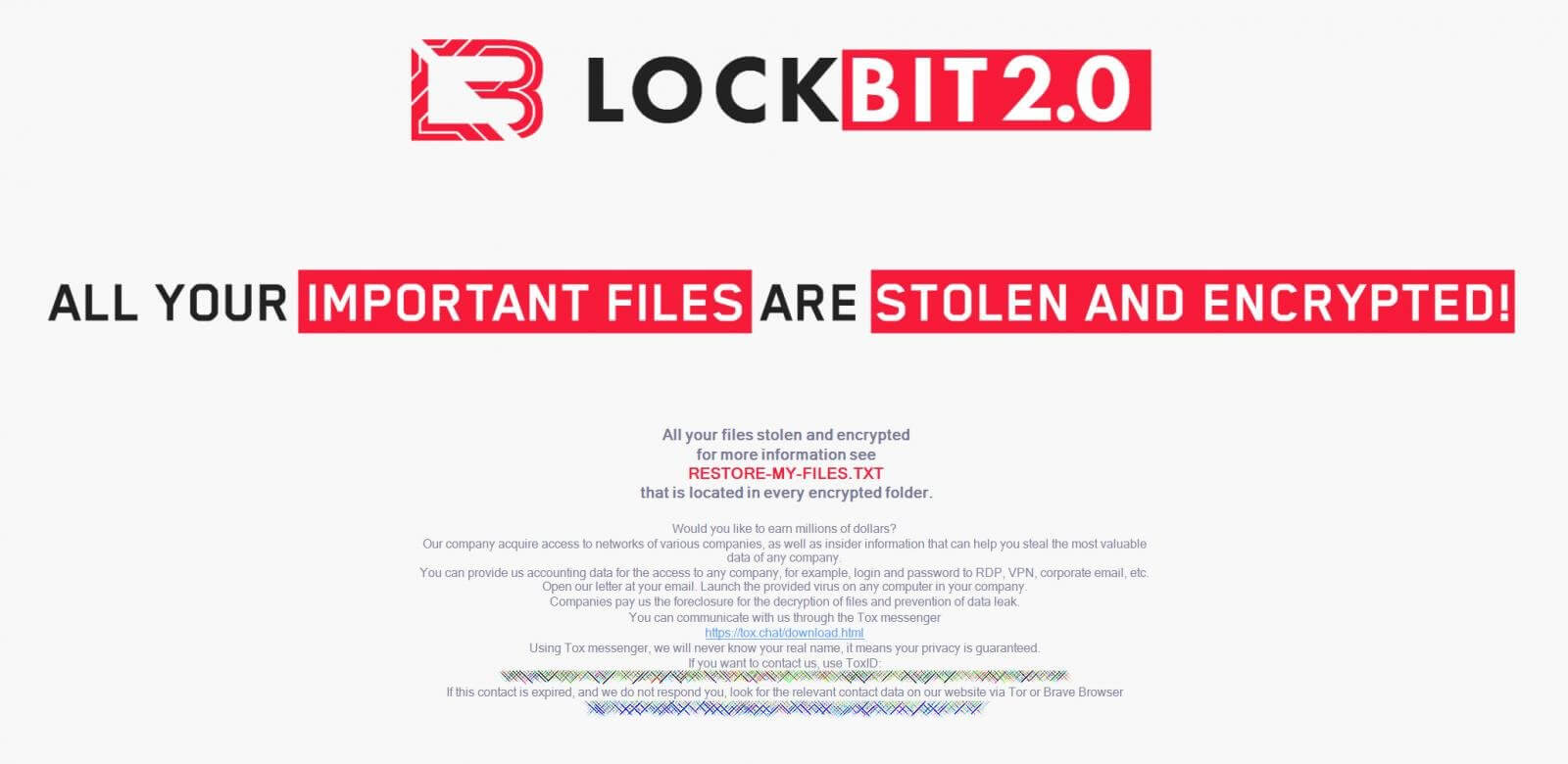
The LOCKBIT 2.0 ransomware group has been highly active in the past few months and It has gained huge popularity among threat actors since the first version of the ransomware family appeared in September 2019. It is distributed via various underground (russian)forums, and targets victims in the United States, Canada, Europe, Asia, and Latin America. LOCKBIT 2.0 developers customize ransomware variants as per their affiliates’ needs. The malware uses the double extortion technique to compel victims into paying ransoms. Through this technique, attackers exfiltrate the victim’s data, after which they proceed to encrypt the data on the victim’s system. Data encryption is followed by the attackers demand ransom in exchange for a decryptor. If the victim refuses or cannot pay the ransom, the attackers threatens to leak the data.The extension used by this ransomware is “.lockbit”.
Technical Analysis
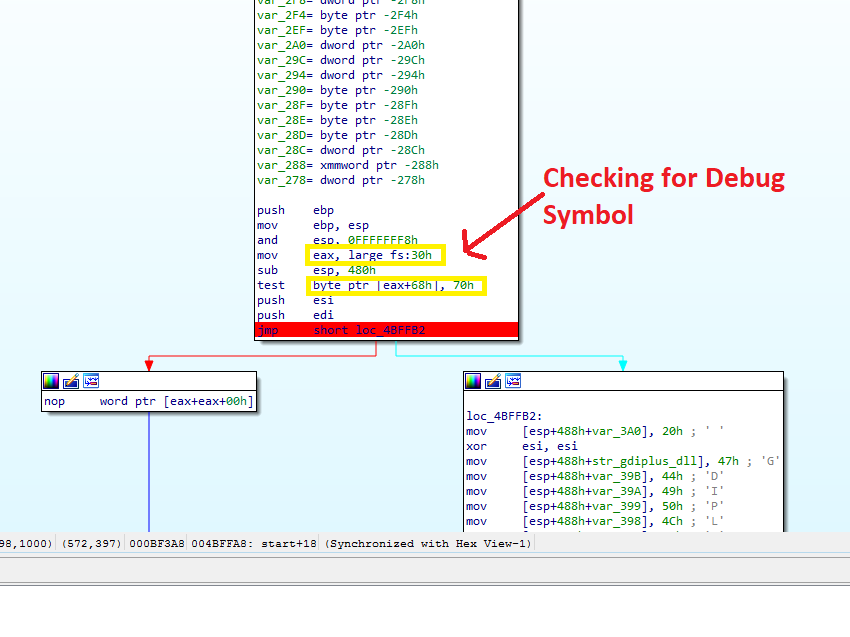
Anti-Debug
From a first glance at the recent LockBit sample with a reverse-engineering tool, we can tell that the program was written primarily in C++ with some additions made using Assembler. For example, a few anti-debug techniques employ the fs:30h function call to manually check the PEB (Process Environment Block) for the BeingDebugged flag, instead of using IsDebuggerPresent().
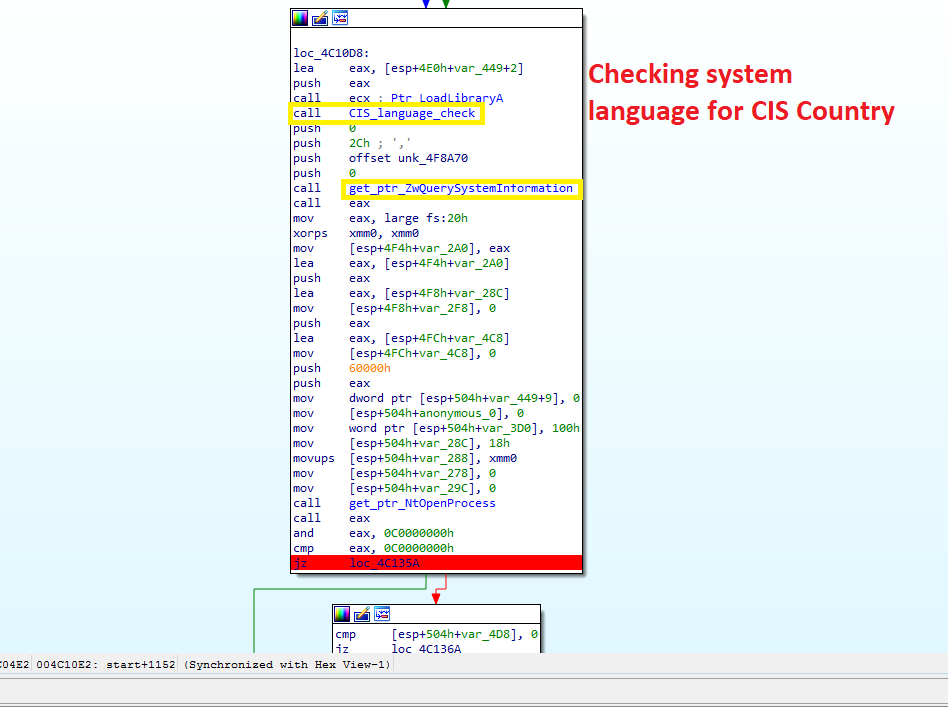
As many other cyber-criminal services, LockBit does not allow the use of the software in any of the CIS countries. This is commonly done to avoid (FSB) prosecution if the threat actor resides in one of those nations. as we have seen previously, CIS authorities don’t bother investigating these groups unless they are operating against targets in their area of jurisdiction.
Creating persistence through Current version Run
If the system is shut down, the malware also has capability to persist after a reboot. LockBit creates a registry key to restart itself under HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
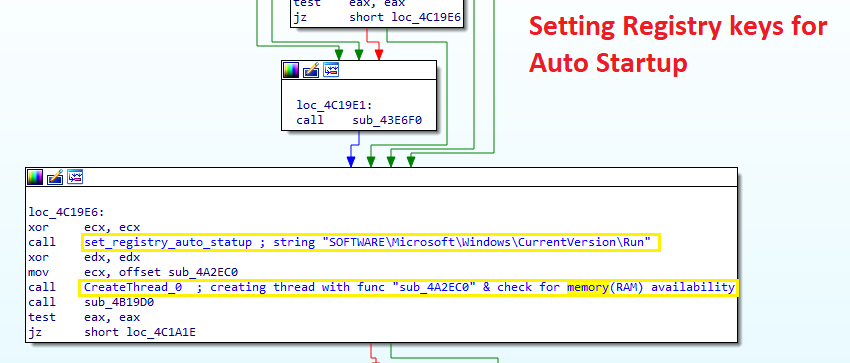
Decrypting String
LockBit ransomware loads its modules dynamically instead of having them hardcoded in the IAT and uses LoadLibraryA. This method is employed to avoid detection by static engines. Names of modules is decrypting at runtime so that they can avoid static analsis and bypass EDR/AV products.
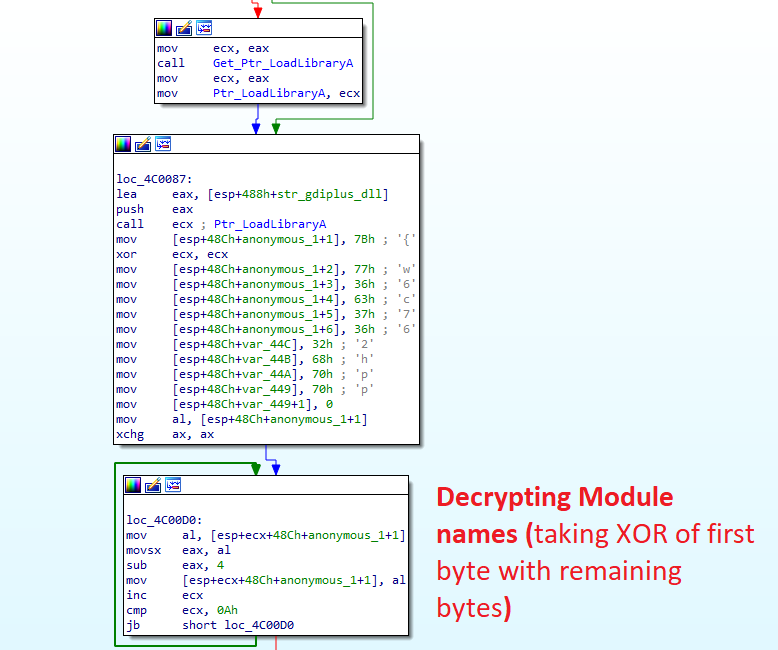
Check your privilege and kill process
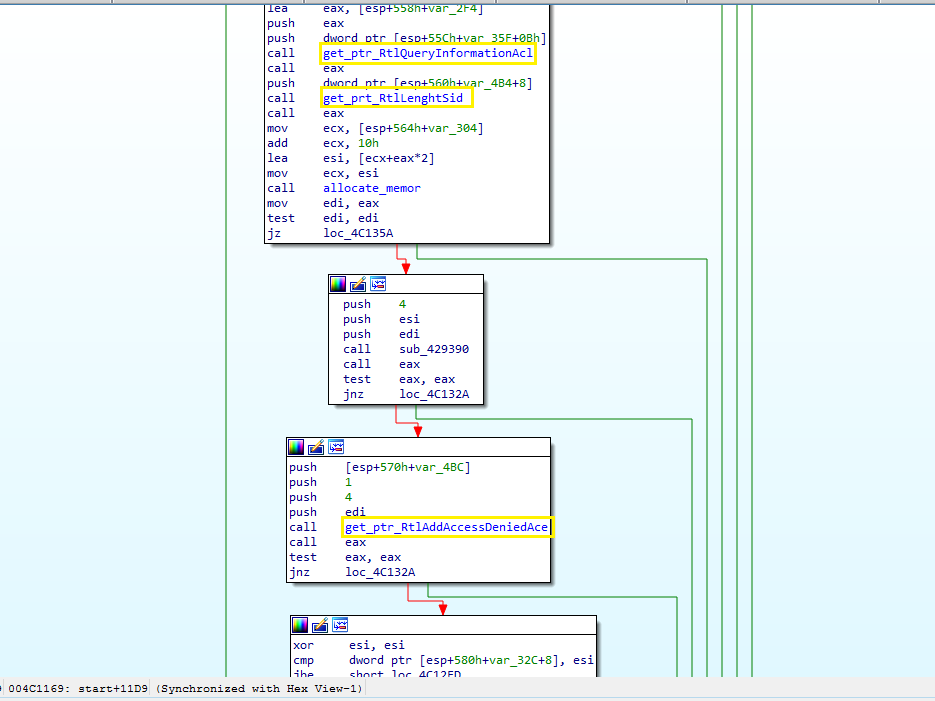
To ensure that it can do the most damage possible, LockBit has a procedure to check whether its process has Administrator privileges. And if it doesn’t, it uses a technique that is growing in popularity among malware developers: a Windows User Account Control (UAC) bypass.
Leveraging OpenProcessToken, it queries the current process via a TOKEN_QUERY access mask. After that, it calls CreateWellKnownSid to create a user security identifier (SID) that matches the administrator group (WinBuiltinAdministratorsSid), so now the malware has a reference it can use for comparisons. Finally, it checks whether the current process privileges are sufficient for Administrator rights, with a call to CheckTokenMembership.
LockBit enumerates the currently running processes and started services via the API calls CreateToolhelp32Snapshot, Process32First, Process32Next and finally OpenProcess, and compares the names against an internal service and process list. If one process matches with one on the list, LockBit will attempt to terminate it via TerminateProcess.
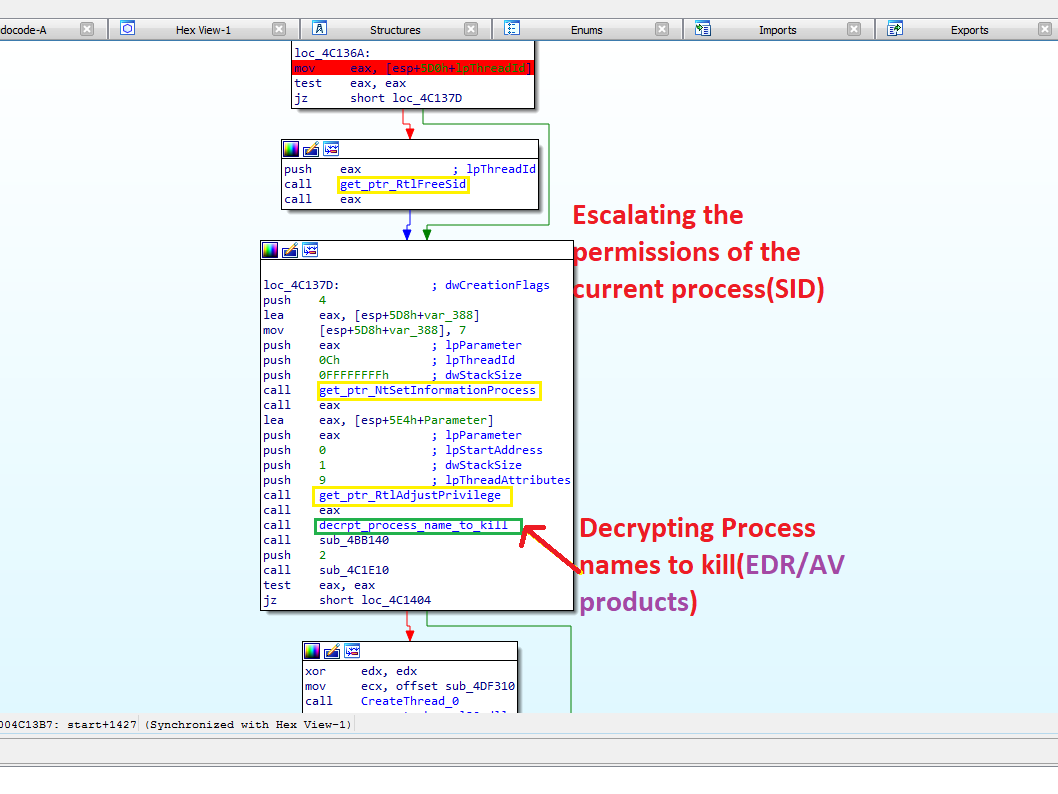
List of Process/Service LockBit tries to kill
| wxServer | wxServerView | sqlmangr | RAgui | supervise |
| Culture | Defwatch | winword | QBW32 | QBDBMgr |
| qbupdate | axlbridge | httpd | fdlauncher | MsDtSrvr |
| java | 360se | 360doctor | wdswfsafe | fdhost |
| GDscan | ZhuDongFangYu | QBDBMgrN | mysqld | AutodeskDesktopApp |
| acwebbrowser | CreativeCloud | Adobe Desktop Service | CoreSync | Adobe CEF |
| Helper | node | AdobeIPCBroker | sync-taskbar | sync-worker |
| InputPersonalization | AdobeCollabSync | BrCtrlCntr | BrCcUxSys | SimplyConnectionManager |
| Simply.SystemTrayIcon | fbguard | fbserver | ONENOTEM | wsa_service |
| koaly-exp-engine-service | TeamViewer_Service | TeamViewer | tv_w32 | tv_x64 |
| TitanV | Ssms | notepad | RdrCEF | sam |
| oracle | ocssd | dbsnmp | synctime | agntsvc |
| isqlplussvc | xfssvccon | mydesktopservice | ocautoupds | encsvc |
| tbirdconfig | mydesktopqos | ocomm | dbeng50 | sqbcoreservice |
| excel | infopath | msaccess | mspub | onenote |
| outlook | powerpnt | steam | thebat | thunderbird |
| visio | wordpad | bedbh | vxmon | benetns |
| bengien | pvlsvr | beserver | raw_agent_svc | vsnapvss |
| CagService | DellSystemDetect | EnterpriseClient | ProcessHacker | Procexp64 |
| Procexp | GlassWire | GWCtlSrv | WireShark | dumpcap |
| j0gnjko1 | Autoruns | Autoruns64 | Autoruns64a | Autorunsc |
| Autorunsc64 | Autorunsc64a | Sysmon | Sysmon64 | procexp64a |
| procmon | procmon64 | procmon64a | ADExplorer | ADExplorer64 |
| ADExplorer64a | tcpview | tcpview64 | tcpview64a | avz |
| tdsskiller | RaccineElevatedCfg | RaccineSettings | Raccine_x86 | Raccine |
| Sqlservr | RTVscan | sqlbrowser | tomcat6 | QBIDPService |
| notepad++ | SystemExplorer | SystemExplorerService | SystemExplorerService64 | Totalcmd |
| Totalcmd64 | VeeamDeploymentSvc |
Encrytion
HKEY_CURRENT_USER\Software\BDCDC5DF1C334E\Public HKEY_CURRENT_USER\Software\BDCDC5DF1C334E\Private
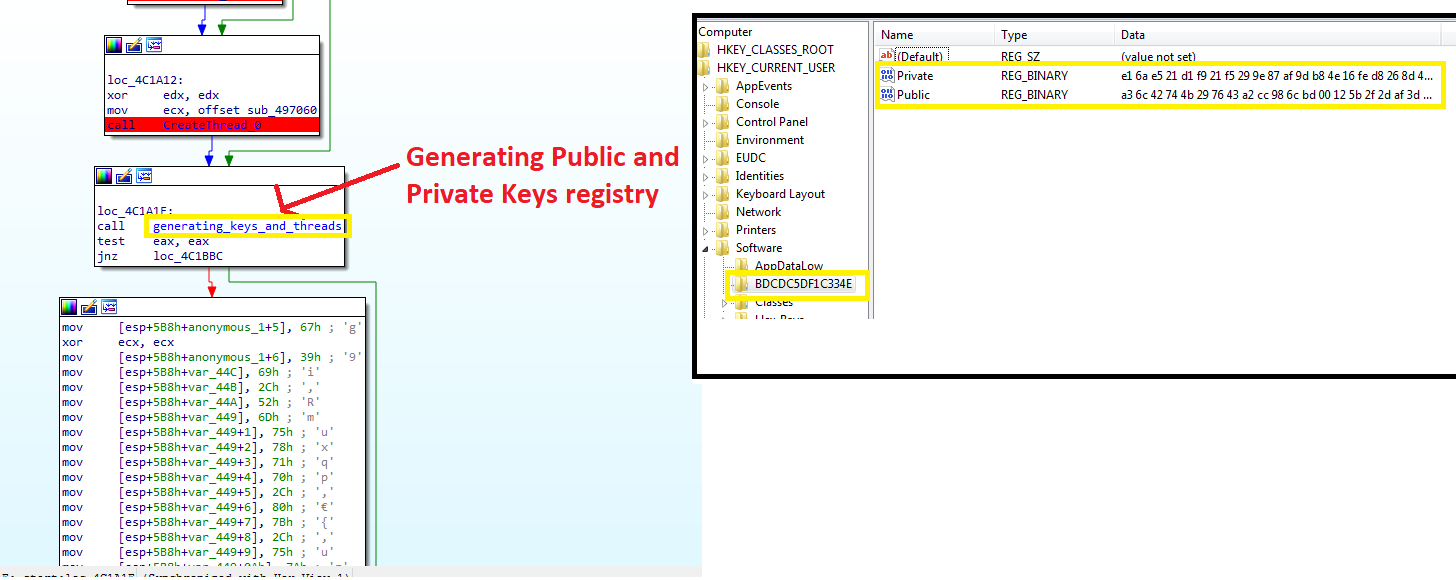
These two registry keys are used as part of the encryption process.
LockBit is using the Input/Output Completion Ports (IOCPs).
IOCPs are a model for creating a queue to efficient threads to process multiple asynchronous I/O requests. They allow processes to handle many concurrent asynchronous I/O more quickly and efficiently without having to create new threads each time they get an I/O request.
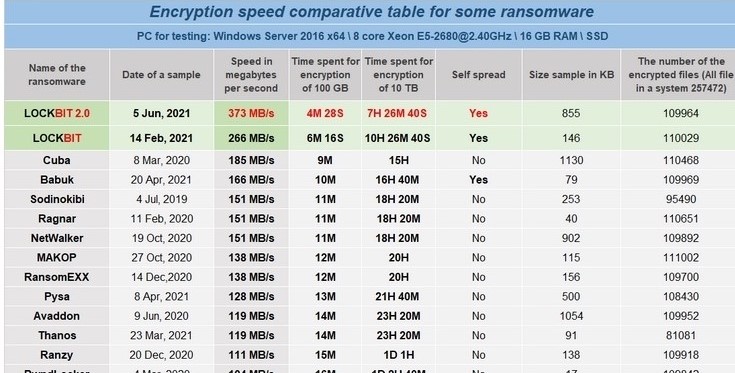
Underground forums
Trust
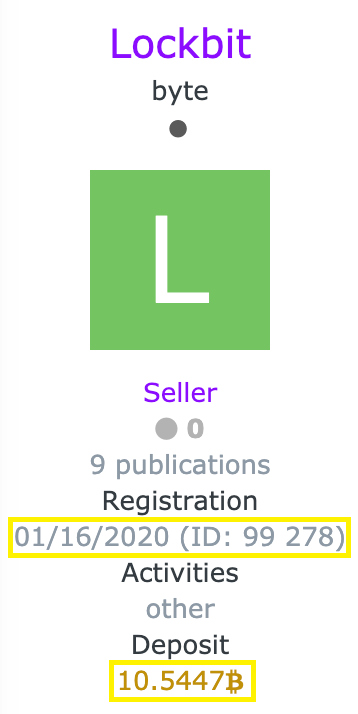
LockBit has joined the underground darkweb forum with a clear determination to do business; the authors have put a down a deposit in excess of 10.5 BTC. Putting a deposit in escrow is a way to demonstrate that the seller is invested financially and not out to scam potential partners.
Support
we can see that the user is quite active currently on underground forums